Member-only story
Secure Uploads to AWS S3 with Ruby on Rails
Do not expose your secrets on the client. The following guide will outline how to upload files directly to S3 without exposing your secret tokens.
Introduction
A direct upload to the storage server (S3, GCP storage, etc) may be desired when working with large files. Since uploading through the server would consume resources with the handling of these long running requests.
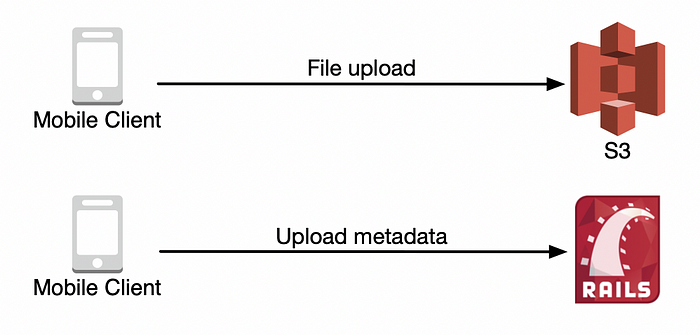
A possible (yet vulnerable) approach to implementing direct uploads is pictured below. In it, a client uploads a file directly to S3 using credentials it already has (usually that allow any upload) and when the upload successfully completes the client makes a POST request to the server indicating a new file has been uploaded. However, this approach exposes the S3 secrets and would allow a bad agent to upload any file (and possibly overwrite existing files).
The addition of an extra step increases the security of the upload by not exposing secrets and allowing the server to validate the request (check authorization, etc). This new flow is shown below.
